
Author: Michael Clark

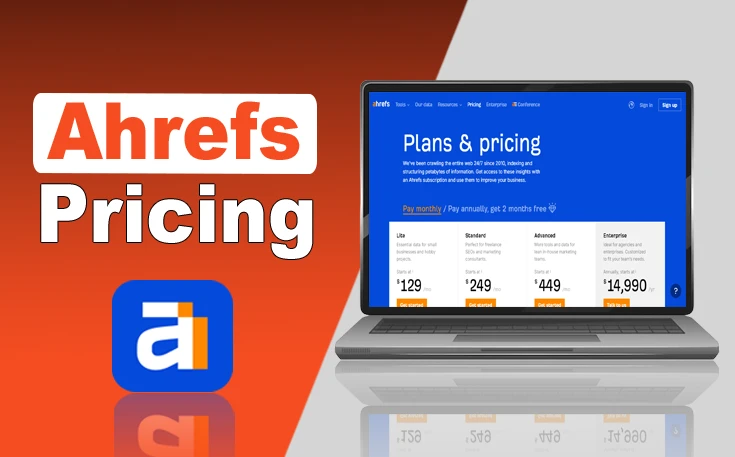
Ahrefs Pricing – What You Get & How to Choose
February 18, 2025
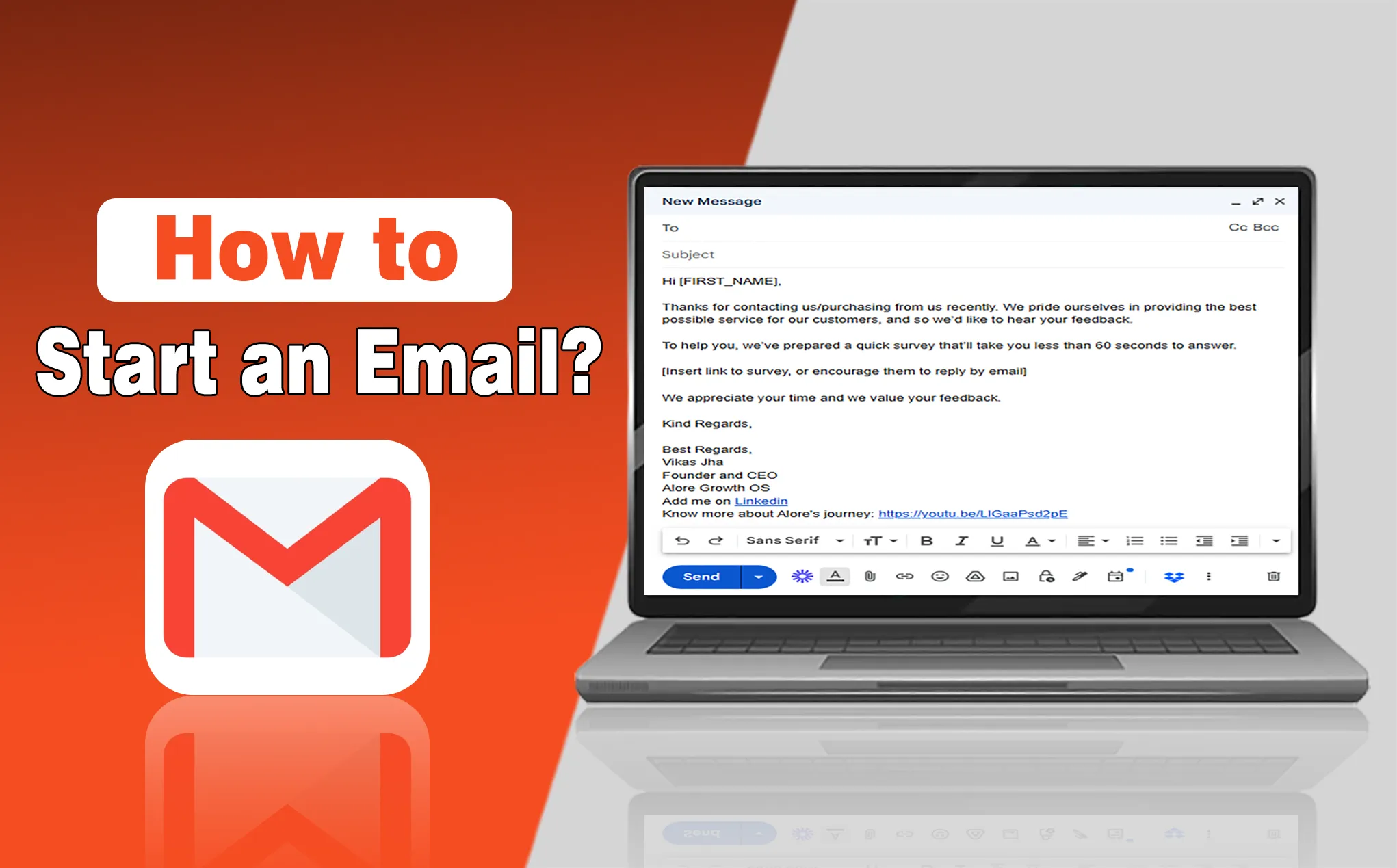
How to Start an Email? Top Tips to Follow
February 5, 2025


10 Best Data Analytics Tools for Businesses
February 5, 2025
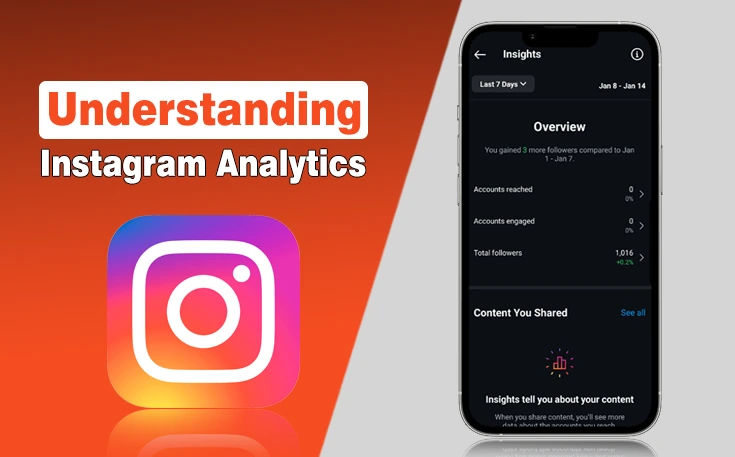

Instagram API Documentation for Beginners Guide
October 27, 2024
Exploring Different Types of Proxies and Their Use
September 12, 2024

How to End an Email to Avoid Rough Phrases?
September 10, 2024

What is Mobile Application Security and Why Is It Important?
September 10, 2024
Webpage Not Available – What Does It Mean and How to Fix It
August 23, 2024

What is Web 3.0 and How Does it Work – A Guide
August 9, 2024

Justoctane SEO Company Boca Raton Services
August 6, 2024

Key Considerations for Hiring an E-commerce SEO Agency
August 3, 2024

What is Connected Marketing? Why You Should Do It
June 29, 2024

A Guide to Evaluate the Value of a Domain Name
May 19, 2024

What Is Coding? Its Role in Web Design
May 14, 2024
